
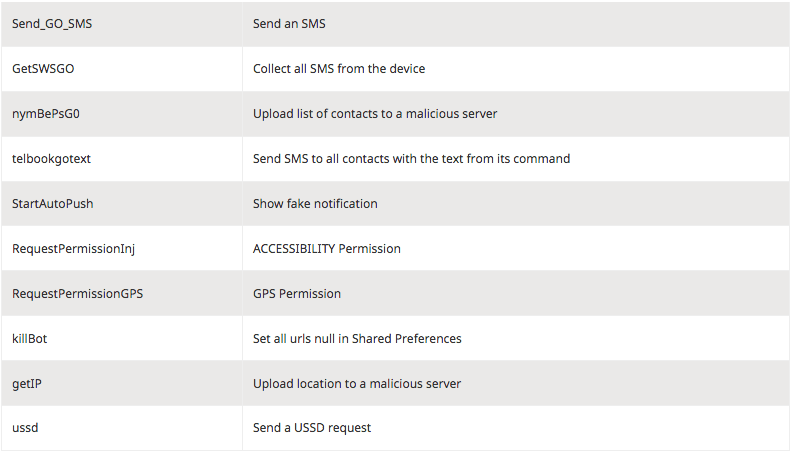
“Like most other Android banking malware, even this one is designed for stealing login credentials, hijacking SMSs, uploading contact lists and SMSs on a malicious server, displaying an overlay screen (to capture details) on top of legitimate apps and carrying out other such malicious activities,” said Quick Heal in the report.
The malware Android.banker.A2f8a is being distributed through a fake Flash Player app on third-party stores. Once if the user installs the malicious app, it will keep on asking the user to activate admin rights. “And even if the user denies the request or kills the process, the app will keep throwing continuous pop-ups until the user activates the admin privilege. Once this is done, the malicious app hides its icon soon after the user taps on it,” the report added.
Once if the user grants admin rights to the application, the application carries out malicious tasks in the background. If it founds out any of the banking application out of the 232 apps installed on the smartphone, it will throw a fake login page by which it steals the login information.
Furthermore, the malicious application has the ability to intercept all incoming and outgoing SMSs from the infected device with which the attackers bypass the two-factor verification. And it also has the ability to transfer all the SMSs for your inbox to the service.
- Axis Mobile
- HDFC Bank MobileBanking
- SBI Anywhere Personal
- HDFC Bank MobileBanking LITE
- iMobile by ICICI Bank
- IDBI Bank GO Mobile+
- Abhay by IDBI Bank Ltd
- IDBI Bank GO Mobile
- IDBI Bank mPassbook
- Baroda mPassbook
- Union Bank Mobile Banking
- Union Bank Commercial Clients



